Select a date to register.
- Online Training
- $595.00
- Friday, January 8, 2021(Guaranteed to Run)
- Tuesday, February 2, 2021(Guaranteed to Run)
- Friday, March 5, 2021(Guaranteed to Run)
- Friday, April 9, 2021(Guaranteed to Run)
- Friday, May 14, 2021(Guaranteed to Run)
Course Description

- Navigate to User Download option to fetch the user database from the AD server. Enable the check box to download Download users and groups and define the time interval about how frequently FMC contacts AD to download user database. Select the group and put it into the Include option for which you want to configure the authentication.
- In FirePOWER Management Center navigate to System Integration Realms and click on New realm. Enter the information required. If you don’t know things like the base DN I suggest you use a directory browser such as LDP.EXE to obtain the correct AD attributes. Check out this post for help with this. Figuring out an Active Directory Objects DN Path.
Watch, interact and learn more about the songs, characters, and celebrities that appear in your favorite FMC Corporation TV Commercials. Watch the commercial, share it with friends, then discover more great FMC Corporation TV commercials on iSpot.tv.
Organizations are increasingly integrating Mac computers into Windows or other standards-based network environments. But users and the IT professionals who support them can relax, because Mac integration is easy.
Course Objectives
Upon completion of the Mac Integration Basics 11 course, students will be able to:
- Integrate a Mac into a Windows network environment.
- Configure a Mac to work with Active Directory.
- Take advantage of network services, file sharing, printing, instant messaging, email, calendars, and contacts.
- Provide security at the user, local-networking, and remote-networking levels.
- Migrate data from a Windows computer to a Mac.
- Back up data.
- Run Windows programs on a Mac.
Who Should Attend?
Fmc Ad Integration Group
- Users who bring a Mac into organizations that predominantly use the Microsoft Windows operating system and Windows Server Essentials
- Users who replace a Windows computer with a Mac
- IT professionals who support Mac users in organizations that predominantly use Windows and Windows Server Essentials
Prerequisites
To have the best learning experience with this course, you should understand how to use a Mac, a Windows computer, and computer peripherals.
Course Outline:
Note: The curricula below comprise activities typically covered in a class at this skill level. The instructor may, at his/her discretion, adjust the lesson plan to meet the needs of the class.
Lesson 1: Directory Services
- Connect a Mac to an Active Directory server.
Lesson 2: Share Files
- Connect to file servers
- Turn on personal file sharing
Lesson 3: Configure Collaborative Services

- Manage Internet Accounts preferences
- Connect to an Exchange Server
- Connect Mail to non-Windows servers
- Add accounts in Mail, Contacts, and Calendars
Lesson 4: Secure a Mac
- Built-In Security Features
- Create strong passwords
- Use two-factor authentication
- Set a firmware password
- Lock a Mac screen
- Create user accounts
- Disable automatic login
- Protect start-up disk files
- Ensure that the apps you download are safe
- Provide network security.
Lesson 5: Printing
- Connect to a local printer
- Connect to, share, and print from network printers
Lesson 6: Move and Back-Up Content
- Move content
- Back up content
Lesson 7: Running Windows on a Mac
- Run Windows natively or virtually
- Microsoft Office for macOS
- Cross-platform apps
- Cross-platform files
RELATED TRAINING
Firepower uses identity policies to detect the user associated with a connection (IP address). The administrator can view usage based on user identity and configure access control policies, allowing or blocking traffic based on user or groups. By identifying the user, you can correlate threat, endpoint and network intelligence with the user identity information.
Username to IP bindings are learnt either using passive or active authentication.
Passive Authentication
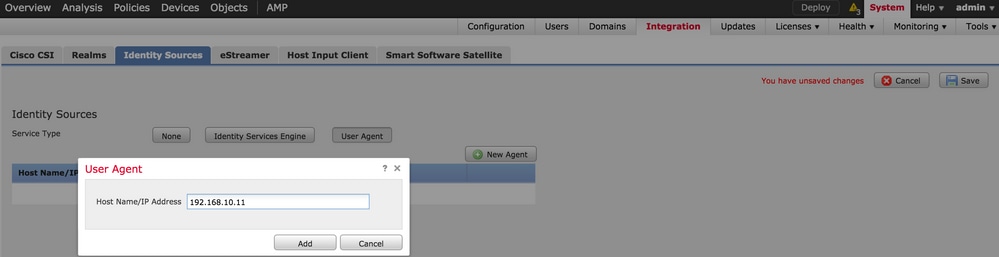
- Use the Firepower User Agent installed on a Windows member server, this agent queries the AD security event logs for user login/logoff events and sends to the FMC
- Alternatively, ISE or ISE-PIC can be integrated with the FMC using pxGrid
- Passive authentication is transparent to the users
Active Authentication
- The user logging into a Firepower captive portal webpage, which in turn authenticates against the user against LDAP/AD.
A “Realm” must be configured on the FMC in order to download from LDAP/Active Directory the user and group.
A “Identity Policy” contains identity rules, they associate the traffic (Source/Destination networks, Zones) with the Realm (authoritative identity source) and the authentication method (active, passive or no authentication). The Identity Policy is referenced within the Access Control Policy and applied to the FTD. The FTD is sent the User/IP bindings and group memberships.
In this post we will cover the steps to configure passive authentication by defining a Realm and Identity Policy. ISE will be used to learn the IP/Username bindings, integration with ISE and FMC was previously covered in the post ISE pxGrid integration with Firepower and will not be covered in this post.
Configure Realms
- Login to the FMC
- Navigate to System > Integration > Realms
- Click New Realm
- Add the appropriate domain details, click Test AD Join to test connectivity
- Click Ok
- Click Add directory
- Add Hostname/IP address of Domain Controller, Port and Encryption
- Click Ok
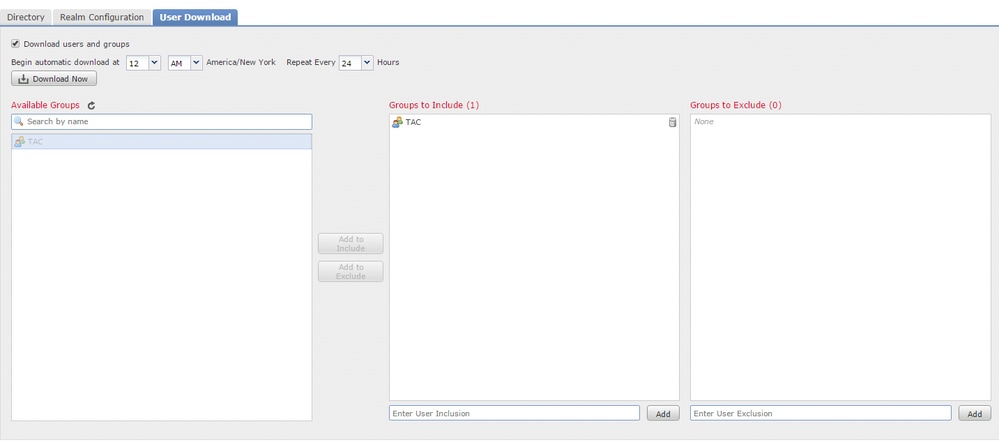
- Click User Download
- Select Download users and groups
If connectivity is successful, the FMC should query AD and download the groups. Cisco recommends that you explicitly include only the groups that represent the users you want in the access control policy.
Available Groups – the group is not downloaded
Groups to Include, the group is downloaded, and user is available for user awareness and user control.
Groups to Exclude, the group name only is downloaded. Users in the group are not downloaded. User data is available for user awareness, but not for user control.
- Select the groups to include and use in the access control policy
- Click Save
- Click the Download Now button to download the groups and users within the group
- Set a schedule to download the users/groups as appropriate.
Create Identity Policy
- Navigate to Policies > Access Control > Identity
- Click Add a new policy
- Name the policy appropriately
- Click add Rule
- Name the Rule
- Define the Action as Passive Authentication
- Ensure Enabled is selected
- Define Zone and Networks
- Click Realms & Settings
- From the Realm drop-down list select the Realm previously created
- Click Save
Modify Access Control Policy
The Access Control Policy must be configured to specifically use the Identity Policy and define which rules will use user identification.
- Navigate to Policies > Access Control > Access Control
- Select the existing Access Control Policy
- Click the Advanced tab
- Edit the Identity Policy Settings
- From the drop-down list select the Identity Policy
- Click Rules
- Create a new rule or modify an existing rule
- Click the Users tab
- Click the Realm name, this should list all available groups and users within the groups
- Select the Group to add to the rule
In this example for testing we will have two ACP Rules, 1 for users that are members of the AD Group Customer1 and another for Customer2.
- Click Save
- Deploy the policy to the FTD
For testing purposes 2 users were logged in simultaneously to 2 computers.
- User1 member of the AD group Customer1, computer IP address 192.168.11.102
- User2 member of the AD group Customer2, computer IP address 192.168.11.101
Login to the CLI of the FTD
- Change to expert mode using the command expert
- Run the command user_map_query.pl -i 192.168.11.101
This command will determine which user is associated with the IP address defined.
From the output we can determine “user2” is associated with the IP address 192.168.11.101. The value (39) is the unique FTD identity ID for user2.
- Change the directory to /ngfw/var/sf/detection_engines/<UUID>
- Run the command cat ngfw.rules to view the Access Control Policy
From the output we can determine that the AD Group “Customer1” is referred to as “group 9” and “Customer2” is referred to as “group 10” in the FTD Policy.
- Exit expert mode
- Run the command system support firewall-engine-dump-identity-data
- Change to expert mode using the command expert
- Change directory to /var/sf/detection_engines/<UID>/instance-1
- View the User Identity dump using the command cat user_identity.dump to view all active users with a session on the FTD
From the output you can determine that the IP address 192.168.11.102 is associated with a User ID #37, this is the AD user “user1”, this user is a member of the Group ID #9, this is the AD Group Customer-1. User2’s User ID #39 and this user is a member of the group ID #10.
- Generate some traffic as user2
- From the CLI of the FTD run the command system support identity-debug enter the client IP address of user2’s computer
From the output we can again determine the User ID #39 for User2 and that the FTD found a passive session.
- From the CLI of the FTD run the command system firewall-engine-debug enter the client IP address of user2’s computer
From the output we can determine the session matching correctly matching rule #13 “Customer2” and traffic is allowed.
Fmc Ad Integration
- On the FMC run the command cat /var/sf/run/adi-health will provide information on the state of the Realm configuration
- Run the command adi_cli session will display the user sessions sent from ISE to the FMC
- Run the command OmniQuery.pl
- Type select * from user_group_map; to list the user to group mappings
From the output we can identify the ID’s of user1 (37) and user2 (39) used in testing and the group associated with the user.
- Type select * from user_group; to list the group mappings
From the output you can determine the current realm ID 4 and the 2 downloaded groups (Customer1 and Customer2). Realm ID 3 was previously used for testing, which is why the output lists the groups.
Cisco Fmc Ad Integration
- Type select * from user_identities; to list the user identities table
Fmc Ad Integration Tools
The output will provide the Realm ID (only relevant if more than one Realm in use), the user ID and the real username.
