Score 8.8 out of 10 0. Based on 23 reviews and ratings. Nessus not only lists out these Vulnerabilities but describes clearly the vulnerabilities in details with its thousands of plugins updated regularly, the tool also recommends solution with practical details of easy implementation. Then de-package the Nessus folder and install using the command: dpkg -i Nessus-8.8.0-ubuntu910amd64.deb During downloading to will see Unpacking Nessus Scanner core components. こんにちは、虎の穴ラボのTYです。 今回は、脆弱性診断を行う Nessus というツールを使用して、自宅での簡単な脆弱性診断を試してみましたので、その手順をご紹介します。 Nessusとは Tenable Network Security社が提供する包括的な脆弱性検知スキャナです。20年からの歴史があり、現在までに約1. F.2 Nessus Scan Results. The following vulnerabilities were reported by Nessus port scan: LDAP servers that are not properly configured allow users to connect to the server and query for information. Explanation: Null Bind is enabled on eDirectory LDAP server by default but can be disabled on the server. To enhance the security of the server.
The following vulnerabilities were reported by Nessus port scan:
LDAP servers that are not properly configured allow users to connect to the server and query for information
Explanation: Null Bind is enabled on eDirectory LDAP server by default but can be disabled on the server. To enhance the security of the server, disable the NULL bind on the LDAP server port 389. For more information, see Configuring LDAP Objects.
LDAP servers that are not properly configured set the directory base as null
Explanation: Information can be picked even without prior knowledge of the directory structure. With the help of Null Bind, an anonymous user can query the LDAP server using tools like “LdapMiner.”
Solution: Although there is no way to disable it, security threat like this can be minimized by disabling Null Bind.
The remote service supports the use of weak SSL ciphers suites
Explanation: The remote host supports the use of SSL ciphers that offer either weak encryption or no encryption at all.
Solution: Reconfigure the affected application, if possible, to avoid use of weak ciphers.
The remote directory server leaks information
Explanation: This host is a NetIQ eDirectory server, and has Browse rights on the PUBLIC object.
Solution: If applications using eDirectory do not depend on having PUBLIC rights, then assign the rights given to PUBLIC to authenticated users (ROOT) only. If this is an external system, it is recommended to block the access to port 524 from the Internet.
SSL certificate is signed with an unknown certificate authority
Explanation: The X.509 certificate of the remote host is not signed by a known public certificate authority. If the remote host is a public host in production, this nullifies the use of SSL as anyone can establish a connection in the middle and attack against the remote host.
Solution: This occurs when the client application does not have the certificate of the certificate authority that signed the server's certificate in its trusted certificate store. Purchase a certificate from a known certificate authority for the server and deploy it. Or, if the server's certificate has been issued either by the tree's organizational certificate authority or by an external or third-party certificate authority, then import or add the certificate authority's certificate in the applications trusted certificate store.
For more information, see “Deciding Which Type of Certificate Authority to Use,” in the NetIQ Certificate Server 3.3 Administration Guide.
No review
No Video
It comes with a huge plugin library with tens of thousands of items you can add to the app in order to expand its capabilities according to your preferences. Nessus is perfect for both small businesses and large organizations as it’s perfectly scalable without being limited by the number of workstations, servers or networks.
It comes with built-in capabilities that not only offer software auditing but also allow you to perform virtual and physical device discoveries. The application can also audit mobile devices to offer complete asset coverage and profiling of the whole business environment, supporting both wired and wireless hardware. As a result, Nessus Home is a reliable application that can accurately detect suspicious behavior or known malware, such as botnets.
- License:
- Platform:
- Publisher:
- File size:
- Updated:
- User Rating:
- Editors' Review:
- Downloads:
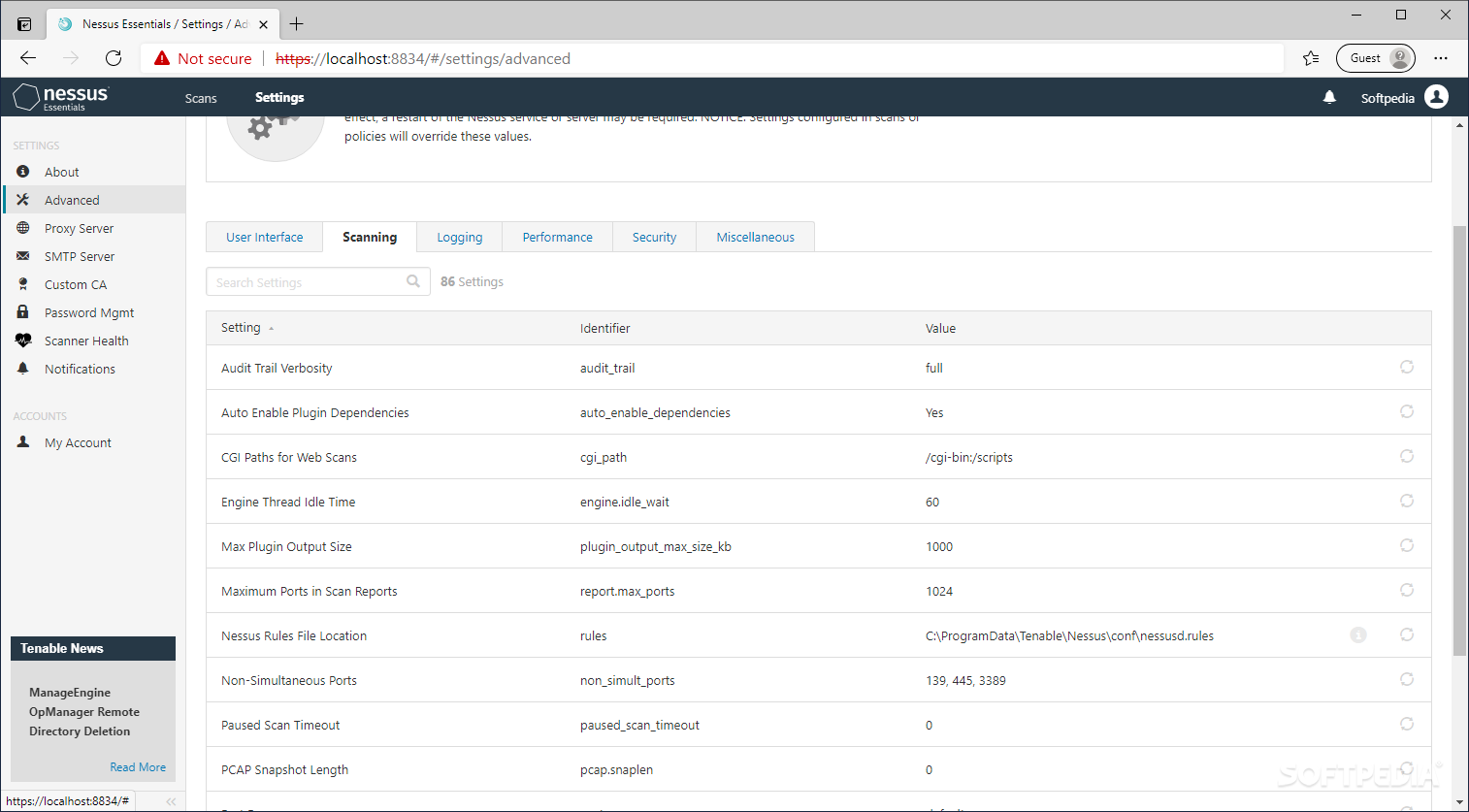
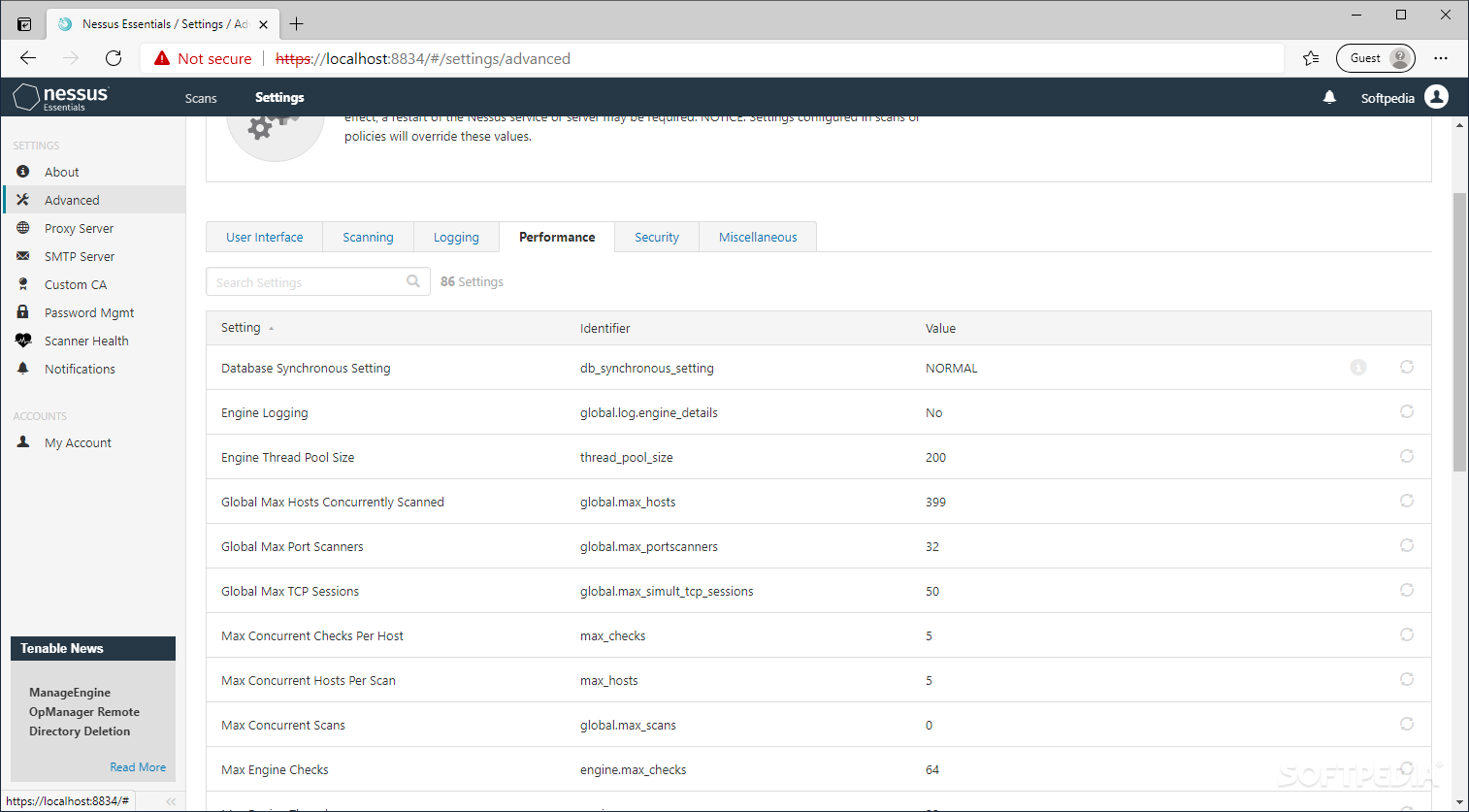
Nessus 8.8.0 Activation Code
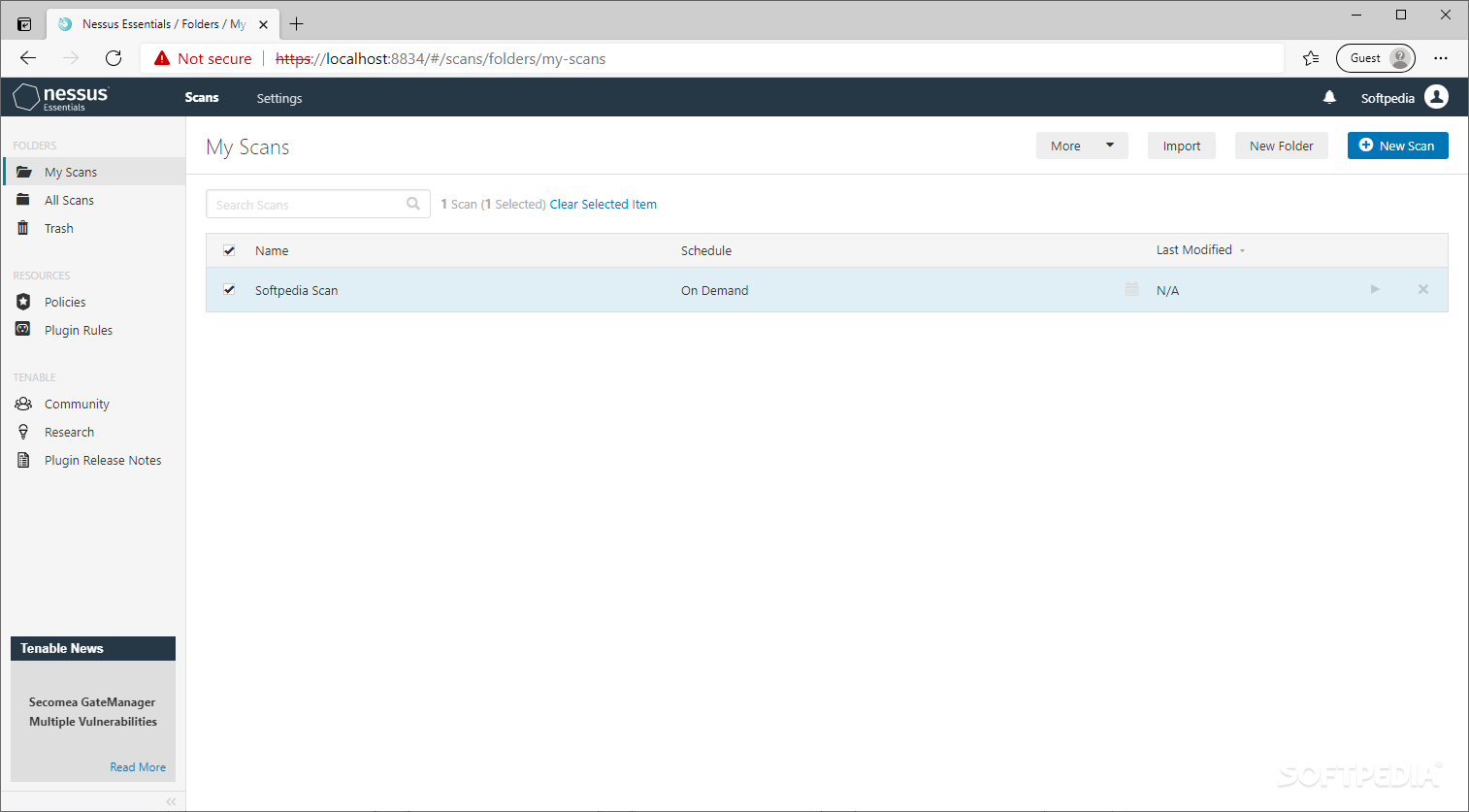
Nessus 8.8 Download

Nessus 8.8 User Guide
