
Split tunneling is used when you want to allow remote VPN users to connect directly to Internet resources while using a corporate VPN instead of routing that traffic through the VPN. Obviously, traffic to the internal corporate LAN still goes through the encrypted VPN tunnel, but other traffic goes directly through the public Internet. There are valid reasons for choosing either to use a split tunnel or not, mainly related to security.
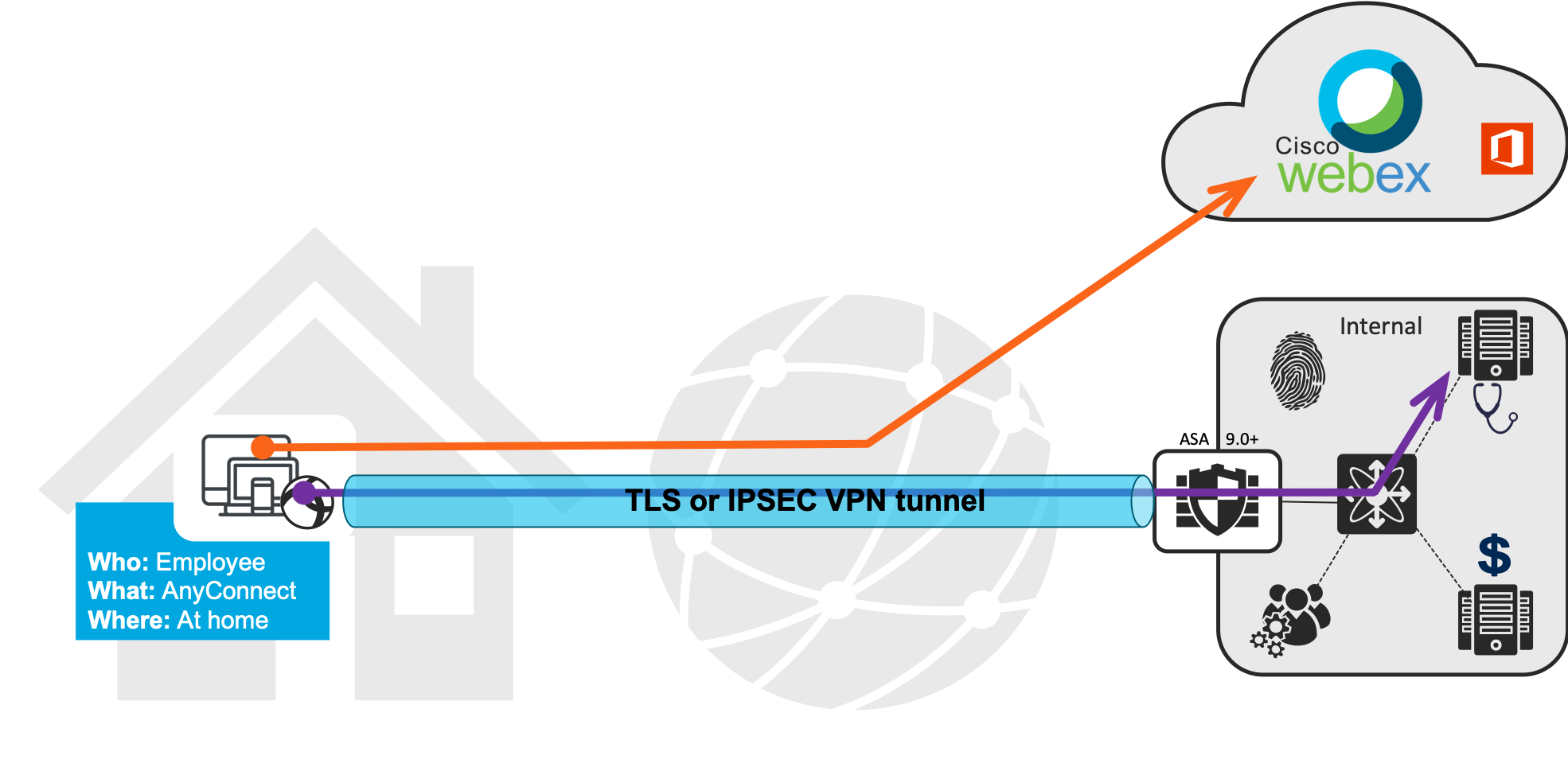
The 'allow split tunneling' is a flexible tool to allow users to have the tunnel to the corporate office, and still browse the internet unencrypted and to access local LAN services like printing and servers. This flexibility comes with a security concern, as the user becomes a getway between Internet threats and corporate network. Split tunneling is a feature used when you want to allow remote VPN users to connect directly to Internet resources without going via VPN tunnel.- Traffic to the internal corporate LAN still goes through the encrypted VPN tunnel, but other traffic goes directly through the public Internet. Mar 30, 2020 Use Dynamic Split Tunneling with AnyConnect to Exclude WebEx from Tunnel Let’s configure this, shall we? I’m going to do all my configuration from ASDM, but you could also do this from Cisco Defense Orchestrator (CDO). In order to use Dynamic Split Tunneling, you must first have some basic or standard Split Tunneling configured.
Split Tunneling Cisco
Examples of Split TunnelingCompanion Video
I've created the following video to show you how to configure a split tunnel on a Cisco ASA security appliance.
Start by creating an access control list to permit a traffic-flow from the internal network:
access-list Split_Tunnel_List standard permit 192.168.101.0 255.255.255.0
Next, enter attributes configuration mode for the desired VPN group policy (in this example, the group-policy name is Account Reps NA):
group-policy 'GroupPolicy_Account Reps NA' attributes
Now, specify the split tunnel mode. You can choose from the following three options:
- excludespecified (exclude only networks specified by split-tunnel-network-list)
- tunnelall (tunnel everything)
- tunnelspecified (tunnel only networks specified by split-tunnel-network-list)
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_Tunnel_List
Watch the video for a complete demonstration of each of the commands.
For More Cisco ASA Configuration Information
Pick up a copy of my configuration guide The Accidental Administrator: Cisco ASA Security Appliance, available through Amazon and other resellers.
Please Leave a Comment
Windows 10 Vpn Split Tunneling
If you find this tutorial helpful or if you notice something that needs to be corrected, please leave a comment.
Cisco Anyconnect Vpn Split Tunneling
The truth is, vpn is great piece of technology and vpn is mine favourite topic in networking.Vpn is amazing tool that can help user to make secure connection to corporate network over an unsecured internet. By default any traffic sent through the VPN network goes through the VPN server in an encrypted manner.Sometimes you need certain traffic should not go through your VPN , That’s why split tunnelling comes into picture.Split Tunneling does exactly the same what its name stands for – Split your Internet traffic.
Split tunneling is a vpn (virtual pirvate network) concept which allows a remote user to access different network domain such as Internet and a local LAN or WAN at the same time, while using the same internet connection.With split Tunneling VPN, you have control to route internet traffic through the VPN network or your local network.
By Default – A Remote VPN software client can route your 100% traffic through vpn sever.But, split-tunnelling feature allow user to select specific traffic to be pushed via a encrypted VPN tunnel , while remaining internet traffic is routed by local internet breakout (Local ISP) as it normally would be.So, this way you can isolate corporate and internet traffic at user-end machine.
Split tunneling come in play when network administrator want to allow remote VPN users to connect directly to Internet resources (browsing, Facebook , email) while using a corporate VPN instead of routing that traffic through the VPN.
Split tunnelling give you control over which traffic in your network get the VPN treatment and which don’t.Split tunnelling refers to the practice of routing only some traffic over the VPN, while let the other traffic directly access the Internet via local internet breakout. Usually, what is routed over the VPN will be traffic destined for internal resources, while web surfing, Facebook , Netflixemail, etc. will go directly to the Internet. The VPN client is configured to route interesting traffic through the tunnel, while using the default gateway of the physical address for everything else.
Split tunnelling allowing a remote VPN user to access a public network (Internet) while accessing corporate resources (server , application) from home or remote locations.With feature of split tunnelling, a vpn user can simultaneously access a public network while connected to a remote access vpn such Cisco any connect or Global protect vpn. In other words, it provides a multi-services access networking path.
Split tunnelling can categorized the network traffic based on how it is configured. A split tunnel configured to only tunnel traffic destined to a specific set of destinations is called a split-include tunnel. When configured to accept all traffic except traffic destined to a specific set of destinations, it is called a split-exclude tunnel.
Split tunnelling involves the configuration of an Access Control List (ACL) that will be associated with this feature. The traffic for the subnets or hosts that is defined on this ACL will be encrypted over the tunnel from the client-end, and the routes for these subnets are installed on the PC routing table.
Split tunnelling is a concept of vpn network that allow administrator to define the traffic of the network (subnet and host) that must be encrypted and routed via tunnel to vpn gateway.
Split tunnelling configuration is involves the configuration of an Access Control List (ACL).
The desire vpn network subnet define in the ACL will be encrypted over the tunnel from the end-user, and the routes for these subnets are installed on the PC routing table.
Related
